Java
CS Table 4/17/2018: Oracle v. Google Ruling
Tue, 2018-04-17 08:49 — petersosWe will revisit the Oracle v. Google case after the recent appeals ruling in favor of Oracle. We will look at the circumstances surrounding the case, revisit definitions of patent and copyright, and try to understand what the ramifications of this decision are for users of Java, Android, open-source software, and the tech sector as a whole.
There are four readings, but if you are pressed for time, we recommend "A Brief History of Oracle v. Google" first and then reviewing the definitions of "Trademark, Patent, and Copyright" as needed.
- A brief article to review the concepts of trademark, patent, and copyright: Trademark, Patent, or Copyright? United States Patent and Trademark Office.
- Read this article to learn about the most recent decision in Oracle v. Google: Susan Decker. Google Could Owe Oracle $8.8 Billion in Android Fight. March 27, 2018. Bloomberg Technology.
- A summary of the history of the Oracle v. Google case: Jonathan Bailey. A Brief History of Oracle v. Google. March 29, 2018. Plagiarism Today.
- For more depth, dive into Wikipedia's history and background on the case: Oracle America, Inc. v. Google, Inc. Wikipedia.
Computer science table (CS Table) is a weekly meeting of Grinnell College community members (students, faculty, staff, etc.) interested in discussing topics related to computing and computer science. CS Table meets Tuesdays from 12:00–12:45pm in JRC 224A (inside the Marketplace). Contact the CS faculty for the weekly reading. Students on meal plans, faculty, and staff are expected to cover the cost of their meals. Visitors to the College and students not on meal plans can charge their meals to the department (sign in at the Marketplace front desk).
- Login to post comments
Thursday Extra: "Enhancing Myro Java using Android"
Mon, 2015-04-13 18:38 — stoneOn Thursday, April 17, Nora Bresette Buccino will discuss the development of an application programming interface for small robots in Java, with extensions to the Android environment:
The use of personal robots in computing is becoming more ubiquitous as robots are a good way to attract students and introduce them to the subject of computer science. Therefore, it is important to make use of all the features of the robots to give users a sense of the capabilities provided by robotics. The API (Application Programming Interface) defined by the Institute for Personal Robots in Education, called Myro, originally created in Python, has now been adapted to many other popular programming languages including Java. The Myro Java API created for the Scribbler robots by Professor Douglas Harms of DePauw University included most of the features of Myro Python. Our goals in this project were to add features to the Myro Java API, to enhance the user's capabilities, and to attempt to incorporate Android development into Myro Java.
Smart phones and tablets have become an integral part of the way we communicate and learn. Not only can these devices be used to communicate with other people, but they can also communicate with other devices through Bluetooth and infrared sensors. Thus these types of devices can interact with devices such as robots and applications can be created to control these robots. Therefore, we decided to integrate Myro and Android to provide the opportunity to not only learn about robotics but to also learn about Android programming and mobile application development.
At 4:15 p.m., refreshments will be served in the Computer Science Commons. The talk, “Enhancing Myro Java using Android,” will begin at 4:30 p.m. in Noyce 3821. Everyone is welcome to attend!
- Login to post comments
Computer Science Table (Friday, April 11, 2014): Lambda expressions in Java 8
Thu, 2014-04-10 11:27 — stoneAs you may have heard, one of the new features of Java 8 is the introduction of anonymous functions (which everyone calls “lambda expressions,” even though there's no lambda in the syntax). This Friday at CS Table, we will explore Java 8's anonymous functions. Here are a few readings you might read or skim in advance of the discussion:
Horstmann, Cay S. “Lambda expressions in Java 8.” Dr Dobb's journal, March 25, 2014.
Weiss, Tal. “The dark side of lambda expressions in Java 8.” The Takipi blog, March 25, 2014.
You may also want to explore the formal tutorial on lambdas:
Oracle. “Lambda expressions.” The Java tutorials, 2014.
Computer Science Table is an open weekly meeting of Grinnell College community members (students, faculty, staff, etc.) interested in discussing topics related to computing and computer science.
- Login to post comments
CSC 207 - Object-Oriented Problem Solving and Algorithms
- Overview
- Catalog Description
- Syllabus Description
- Class Format and Pedagogy
- Current and Past Offerings
- Student Learning Outcomes
CSC 151, CSC 161, and CSC 207 — the three courses in Grinnell's multi-paradigm, introductory computer science sequence — have been recognized as "exemplar courses" by the ACM/IEEE-CS Task Force on Computing Curricula 2013.
Overview
CSC 207 is the third course in Grinnell's introductory computer science sequence and serves as the core gateway
course to the majors. Students develop and analyze core data types (lists, stacks, queues, heaps, trees) and algorithms (primarily sorting and searching). Students also develop facility with object-oriented design. We use the Java programming language.
Starting in Fall 2013, CSC 207 has an experimental theme of Computing for Social Good. Students will work with free and open source projects that relate to the primary content of the course. We will leverage the Android platform for some of this development.
Catalog Description
An introduction to the ideas and practices of computation: message passing, information hiding, classes and interfaces, inheritance, polymorphism, and reflection. The course also includes data structures and the associated algorithms, packages and libraries, exceptions, and the use of an integrated software-development environment. Includes formal laboratory work.
Syllabus Description
Coming Soon
Class Format and Pedagogy
Coming Soon
Current and Past Course Offerings
The department maintains a page of current and past course offerings.
- Full listing of current and past computer science courses
- Listing of current and past offerings of CSC 207
Student Learning Outcomes
Computer Science Curricula 2013 (CS2013), national curricular recommendations from the ACM/IEEE-CS professional societies, identify an extensive list of learning outcomes for undergraduate computer science programs. Upon completing CSC 161, students should achieve the following learning outcomes with the specified level of mastery:
| Knowledge Unit | Learning Outcome with [Level of Mastery] |
| Basic Analysis |
|
| Algorithmic Strategies |
|
| Fundamental Data Structures and Algorithms |
|
| Advanced Data Structures Algorithms and Analysis |
|
| Fundamentals |
|
| Processing |
|
| Graphs and Trees |
|
| Defensive Programming |
|
| Data Modeling |
|
| Object-Oriented Programming |
|
| Functional Programming |
|
| Basic Type Systems |
|
| Advanced Programming Constructs |
|
| Algorithms and Design |
|
| Fundamental Programming Concepts |
|
| Fundamental Data Structures |
|
| Development Methods |
|
| Requirement Engineering |
|
| Software Design |
|
| Software Construction |
|
| Software Verification Validation |
|
| Cross-Layer Communications |
|
| Social Context |
|
| Professional Ethics |
|
| Professional Communication |
|
Introductory courses
Multi-paradigm Approach for Introductory Courses
Computing has become widespread in today's society, largely because it helps people solve problems. However, different types of problems require fundamentally different approaches for problem solving. Computer science recognizes at least four problem-solving approaches as being fundamental to work in the discipline. Each approach involves a distinct way of thinking, and each is supported by a range of computer languages.
Grinnell's computer science curriculum explores several of these paradigms in the beginning courses, each of which has been named a "course exemplar" by the international professional computing societies.
-
CSC 151, Functional Problem Solving
- emphasizes functional problem solving
- supported by the Scheme programming language (a dialect of LISP, a language widely used for artificial intelligence, graphical manipulations, and other applications)
- current application areas: data science, digital humanities
- past application area: image processing / media scripting

|
|

|
|
| CSC 151 image by James Kent and Chris Re-Scherer, Fall 2012 | CSC 151 image by Amy Tsui and Solomon Miller, Spring 2010 | CSC 161 image by Mai Ha Vu, Fall 2012 | CSC 151 image by Grace Philipp, Elizabeth Reischmann, and Lauren Cantley, Fall 2009 |
- CSC 161, Imperative Problem Solving and Data Structures
- studies concepts tied to the architecture of computers, compilers, and operating systems within the context of the imperative problem-solving paradigm
- supported by the C (a programming language widely used in scientific applications and engineering)
- application area: control of robots
|
Scribbler 2 robot (front view) |
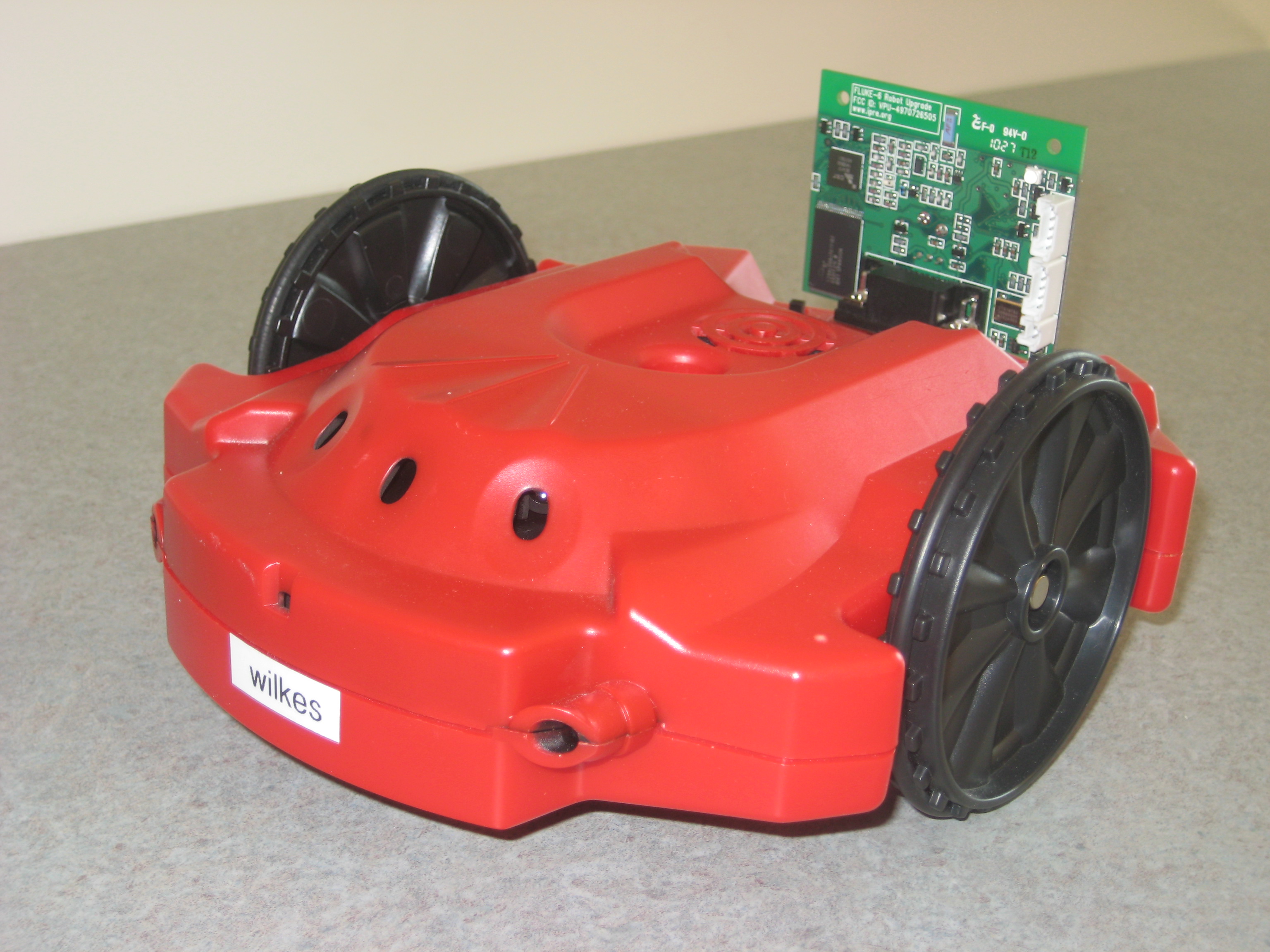
|
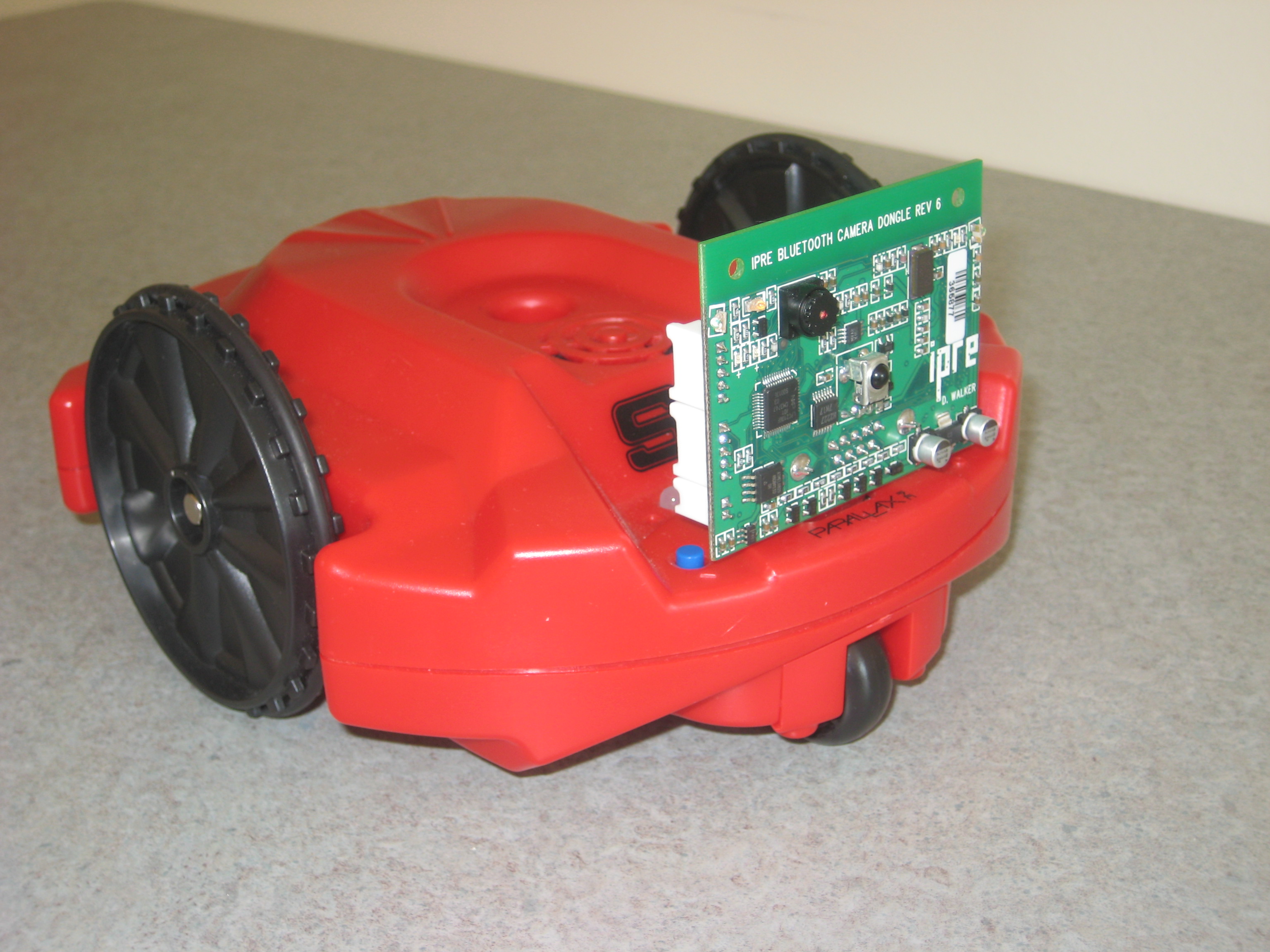
|
Scribbler 2 robot (rear view) |
-
CSC 207, Algorithms and Object-Oriented Design
- explores object-oriented problem solving
- supported by the Java programming language (a language widely use for large-scale applications and systems)
- application area: software development for the common good

Students with considerable background should consult the computer science faculty regarding placement.
- Students with strong scores on the AP CS A examination or the IB CS examination receive credit for their prior work, but placement requires discussion of their specific background.
- Most incoming students find functional problem solving to be quite new and different, so they begin with CSC 151 (where no computing background is assumed).
- Students with substantial experience in imperative problem solving or object-oriented problem solving (e.g., students with AP CS A or IB CS background) may be able to skip CSC 161 or CSC 207, depending upon the extent of their background.
Later courses build on this foundation to provide depth in each of these problem-solving paradigms and programming languages.
